Cyberattack Impact Analysis

Cdk cyberattack update – The CDK cyberattack has had a significant impact on affected organizations and industries, resulting in substantial financial losses, operational disruptions, and reputational damage.
The recent CDK cyberattack update highlights the growing threat to our digital infrastructure. Amidst the chaos, a separate incident has emerged in Tenerife, where British tourist Jay Slater has gone missing. While the authorities continue to investigate the cyberattack, concerns linger over Slater’s whereabouts.
The disappearance has cast a shadow over the ongoing CDK cyberattack update, underscoring the need for vigilance in both the digital and physical realms.
According to a report by cybersecurity firm Mandiant, the attack caused an estimated $100 million in damages to affected organizations, including downtime, data loss, and recovery costs.
Amidst the ongoing developments in the CDK cyberattack, one notable aspect has been the rise of individuals like John Force , who have emerged as key figures in unraveling the complexities of this digital threat. Their expertise and dedication to understanding the nuances of these attacks have been instrumental in mitigating their impact and safeguarding vulnerable systems.
Financial Consequences
- Downtime costs: The attack caused widespread downtime for affected organizations, resulting in lost productivity and revenue.
- Data loss costs: The attackers exfiltrated sensitive data from affected organizations, which could lead to financial losses due to regulatory fines, legal liability, and reputational damage.
- Recovery costs: Affected organizations incurred significant costs in recovering from the attack, including hiring cybersecurity experts, implementing new security measures, and restoring lost data.
Operational Consequences
- Disrupted operations: The attack disrupted operations for affected organizations, including manufacturing, supply chain management, and customer service.
- Loss of trust: The attack eroded trust in affected organizations, as customers and partners became concerned about the security of their data.
- Reputational damage: The attack damaged the reputation of affected organizations, making it difficult to attract new customers and partners.
Technical Details and Mitigation Strategies
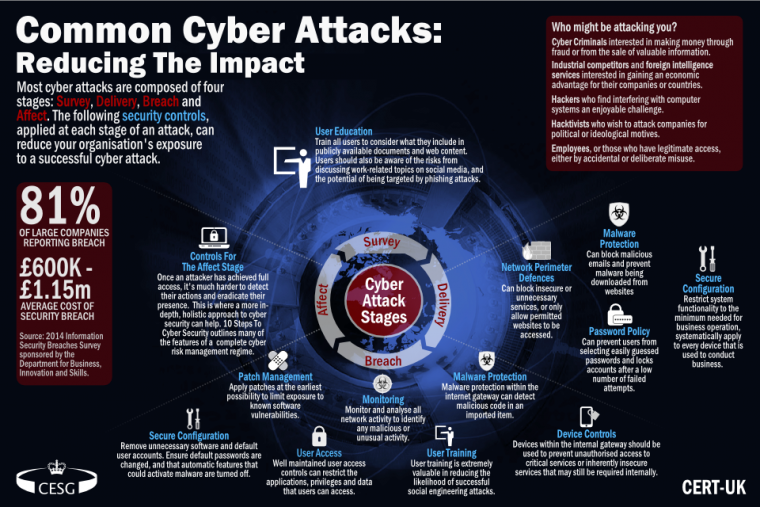
The CDK cyberattack exploited a critical vulnerability in the software’s authentication mechanism, allowing attackers to gain unauthorized access to sensitive data and systems.
Specifically, the attackers exploited a buffer overflow vulnerability in the CDK’s authentication module. This vulnerability allowed them to execute arbitrary code on the target system, giving them complete control over the system.
Mitigation Strategies
Organizations can take several steps to mitigate the risk of similar attacks in the future:
- Implement strong authentication measures, such as multi-factor authentication.
- Keep software up to date with the latest security patches.
- Use a web application firewall to block malicious traffic.
- Implement an incident response plan to quickly respond to and recover from attacks.
By following these best practices, organizations can significantly reduce the risk of falling victim to a similar cyberattack.
Importance of Cybersecurity Measures, Cdk cyberattack update
The CDK cyberattack highlights the importance of cybersecurity measures for organizations of all sizes. Cybersecurity measures can help to protect sensitive data, prevent financial losses, and maintain business continuity.
Organizations should invest in cybersecurity measures to protect themselves from the growing threat of cyberattacks.
Industry Response and Policy Implications: Cdk Cyberattack Update

The CDK cyberattack has sent shockwaves through the cybersecurity industry and government agencies, prompting a swift response and a renewed focus on collaboration and policy changes.
The industry has come together to share information, analyze the attack, and develop mitigation strategies. Cybersecurity firms have released patches and updates to address the vulnerabilities exploited by the attackers. Government agencies, including the FBI and the Cybersecurity and Infrastructure Security Agency (CISA), have issued warnings and guidance to help organizations protect themselves.
Lessons Learned and Collaboration
The CDK cyberattack has highlighted the need for improved collaboration between the cybersecurity industry, government agencies, and organizations.
- Information sharing: The attack has shown that timely and effective information sharing is critical for mitigating cyber threats. The industry and government agencies need to establish mechanisms for sharing threat intelligence, best practices, and incident response plans.
- Joint exercises: Regular joint exercises between the industry and government agencies can help improve coordination and response capabilities in the event of a cyberattack.
Policy Changes and Regulations
The CDK cyberattack has also raised questions about the adequacy of existing cybersecurity policies and regulations.
- Data security standards: The attack has highlighted the need for stronger data security standards that require organizations to implement robust cybersecurity measures and regularly patch their systems.
- Cybersecurity insurance: The attack has also raised the issue of cybersecurity insurance. Organizations need to consider purchasing cybersecurity insurance to mitigate the financial impact of cyberattacks.
As the CDK cyberattack update unfolds, questions linger about the former president’s health. Did Jimmy Carter pass away, as some have speculated? Find out here. The cyberattack’s impact continues to reverberate, with experts emphasizing the need for vigilance and robust cybersecurity measures.
The CDK cyberattack update has raised concerns about the vulnerability of critical infrastructure. In this regard, security expert Quincy Wilson has emphasized the need for robust cybersecurity measures to protect against such attacks. The ongoing investigation into the CDK cyberattack is expected to shed light on the tactics and motivations behind these threats, enabling us to strengthen our defenses and prevent future incidents.
The ongoing CDK cyberattack continues to evolve, with experts closely monitoring the situation. Security researcher Barnabas Varga (more info) has provided valuable insights into the attack’s methods and potential impact. The investigation is ongoing, and authorities are working to mitigate the threat and protect vulnerable systems.